Introduction
SIPp is a powerful open-source traffic generator for the SIP protocol. In this post, we’ll pull the latest release from GitHub, build it with your choice of features (SSL, PCAP, SCTP), and install the sipp binary such that it’s available system-wide.
Prerequisites
- A Debian/Ubuntu server or VM
- Root (or sudo) access
- Internet connectivity
1. Prepare your workspace
Choose a directory where you’ll download and build SIPp. Commonly, /usr/local/src is used for third-party source builds:
cd /usr/local/src
2. Grab the latest release tag
We’ll use the GitHub API so you always get the newest stable version:
LATEST_TAG=$(curl -s https://api.github.com/repos/SIPp/sipp/releases/latest \
| grep '"tag_name":' \
| cut -d '"' -f 4)
This stores something like v3.7.3 in $LATEST_TAG.
3. Download & unpack the tarball
Strip the leading “v” for the filename and pull down the .tar.gz:
VERSION=${LATEST_TAG#v}
wget -c https://github.com/SIPp/sipp/releases/download/"$LATEST_TAG"/sipp-"$VERSION".tar.gz
tar xvf sipp-"$VERSION".tar.gz
cd sipp-"$VERSION"
4. Install build dependencies
Make sure your package index is fresh, then install the tools and libraries SIPp can leverage:
sudo apt update
sudo apt install -y build-essential libncurses-dev libssl-dev \
libpcap-dev libnet1 lksctp-tools libsctp-dev cmake
- build-essential: GCC, make, etc.
- libssl-dev: TLS support
- libpcap-dev: PCAP capture/playback
- libsctp-dev: SCTP transport
5. Configure & compile
Run CMake to generate your Makefiles, enabling SSL, PCAP, and SCTP:
cmake . -DUSE_SSL=1 -DUSE_PCAP=1 -DUSE_SCTP=1
make
If you only need basic SIP messaging, you can omit the corresponding -DUSE_… flags.
6. Install the binary
Copy the resulting sipp executable into your system’s PATH:
sudo cp sipp /usr/local/bin
Now you can run sipp from anywhere:
sipp -h
Basic SIPp Commands
Once you’ve got /usr/local/bin/sipp in place, here are a few handy commands to get you started:
Dump a built-in scenario to XML
# Export the “uac.xml” scenario template to your current directory
sipp -sd uac > uac.xml
This writes out the “user-agent client” (UAC) scenario so you can customize call flows.
Run SIPp as a UAC (client)
# Act as a SIP client, sending REGISTERs or INVITEs to 192.0.2.1:5060
sipp -sn uac 192.0.2.1:5060
Replace 192.0.2.1 with your SIP server’s address (and append -s <user> or other flags as needed).
Run SIPp as a UAS (server)
# Listen on port 5060 for incoming calls, using the built-in UAS scenario
sipp -sn uas -i 0.0.0.0 -p 5060
Here -i sets the local interface and -p the port. UAS will reply to INVITEs using the default server behavior.
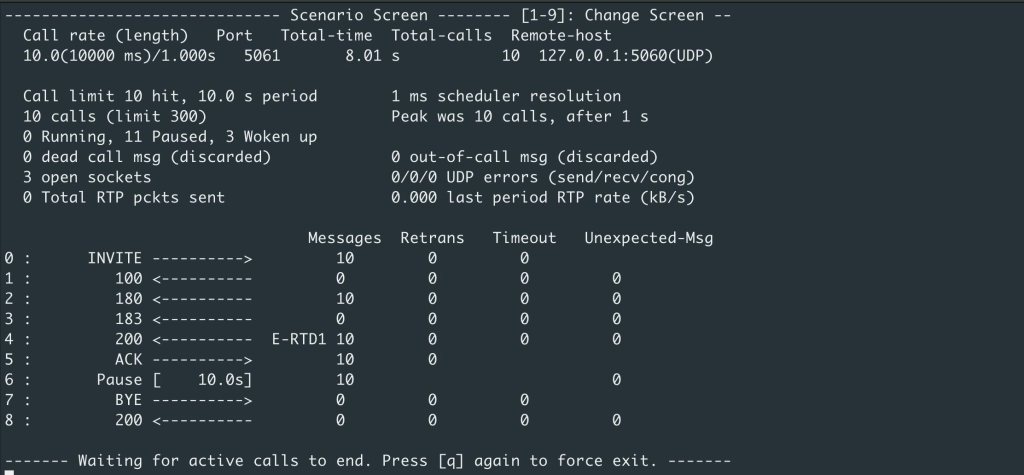
Quick Loopback Test
To quickly
1. Terminal #1 (UAS/server)
sipp -sn uas
2. Terminal 2 (UAC/client)
sipp -sn uac 127.0.0.1 -m 10 -d 10000
-m 10 → send 10 calls
-d 10000 → 10 000 ms call duration
You should see INVITE/OK/ACK sequences and then a clean teardown—confirming your build is working end-to-end.
Additional Links
SIPp Github Repo – link
SIPp Documentation – link
Conclusion
You’ve built and installed the latest SIPp release from source! This approach ensures you always get new features and bug fixes without waiting for distro packages.
Happy testing!
Akash Gupta
Senior VoIP Engineer and AI Enthusiast

AI and VoIP Blog
Thank you for visiting the Blog. Hit the subscribe button to receive the next post right in your inbox. If you find this article helpful don’t forget to share your feedback in the comments and hit the like button. This will helps in knowing what topics resonate with you, allowing me to create more that keeps you informed.
Thank you for reading, and stay tuned for more insights and guides!
Leave a comment